Simple hack to disable USB drives in Windows XP
| There is a simple registry change that will keep the USB storage drivers from starting when the system boots. Keeps people from walking up to a PC and copying data off with a USB key, but allows you to keep your scanner, keyboard, and mouse working. Just open regedit and browse to this key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UsbStor Notice the value 'Start' Switch this value to 4, and USB storage devices are disabled. Switch this value to 3, and USB storage devices are enabled. | |
"There are no foolish questions, only foolish answers" |
Posted on
Friday, February 27, 2009
by
j lo,
under
tips and trick,
troubleshooting,
tutorials.
0
comments.
![]()
Mcdonald & KFC Secret Recipe
 Secret recipes of McDonald and KFC so that you can make them at home!
Secret recipes of McDonald and KFC so that you can make them at home!
Download:
here is the link: http://rapidshare.com/files/21936572/mcdokfc.rar
Posted on
by
j lo,
under
foods,
general info..
1 comments.
![]()
How to delete the "Recycle Bin" in the Desktop
For XP/2003
1. Open Registry Editor.
2. Navigate to this registry.
Code: ‹ Select ›
3. Delete this key
Code: ‹ Select ›
Note: As always, before making changes to your registry you should always make sure you have a valid backup. In cases where you're supposed to delete or modify keys or values from the registry it is possible to first export that key or value(s) to a .REG file before performing the changes.
4. Close Registry Editor. You don't need to restart/reboot your PC, just go to the desktop and refresh!
5. In order to restore the Recycle Bin icon to the desktop just import it back to the registry in case you've exported it earlier.
For Vista
The Recycle Bin icon is horrible and I hate it. Windows Vista has an even simpler way to hide the icon than XP does, but why couldn't they have disabled it by default?
Right-click and delete. It's as simple as that.
Enjoy!
Posted on
by
j lo,
under
general info.,
knowledge database,
tips and trick,
tutorials.
0
comments.
![]()
Definition of Malwares
| Malware - Malware is programming or files that are developed for the purpose of doing harm. Thus, malware includes computer viruses, worms, Trojan horses, spyware, hijackers, and certain type of adware. This tutorial will focus on those malware that are considered viruses, trojans, worms, and viruses, though this information can be used to remove the other types of malware as well. We will not go into specific details about any one particular infection, but rather provide a broad overview of how these infections can be removed. For the most part these instructions should allow you to remove a good deal of infections, but there are some that need special steps to be removed and these won't be covered under this tutorial. Before we continue it is important to understand the generic malware terms that you will be reading about. Adware - A program that generates popups on your computer or displays advertisements. It is important to note that not all adware programs are necessarily considered malware. There are many legitimate programs that are given for free that display ads in their programs in order to generate revenue. As long as this information is provided up front then they are generally not considered malware. Backdoor - A program that allows a remote user to execute commands and tasks on your computer without your permission. These types of programs are typically used to launch attacks on other computers, distribute copyrighted software or media, or hack other computers. Dialler - A program that typically dials a premium rate number that has per minute charges over and above the typical call charge. These calls are with the intent of gaining access to pornographic material. Hijackers - A program that attempts to hijack certain Internet functions like redirecting your start page to the hijacker's own start page, redirecting search queries to a undesired search engine, or replace search results from popular search engines with their own information. Spyware - A program that monitors your activity or information on your computer and sends that information to a remote computer without your knowledge. Trojan - A program that has been designed to appear innocent but has been intentionally designed to cause some malicious activity or to provide a backdoor to your system. Virus - A program that when run, has the ability to self-replicate by infecting other programs and files on your computer. These programs can have many effects ranging from wiping your hard drive, displaying a joke in a small box, or doing nothing at all except to replicate itself. These types of infections tend to be localized to your computer and not have the ability to spread to another computer on their own. The word virus has incorrectly become a general term that encompasses trojans, worms, and viruses. Worm - A program that when run, has the ability to spread to other computers on its own using either mass-mailing techniques to email addresses found on your computer or by using the Internet to infect a remote computer using known security holes. How these infections start Just like any program, in order for the program to work, it must be started. Malware programs are no different in this respect and must be started in some fashion in order to do what they were designed to do. For the most part these infections run by creating a configuration entry in the Windows Registry in order to make these programs start when your computer starts. Unfortunately, though, in the Windows operating system there are many different ways to make a program start which can make it difficult for the average computer user to find manually. Luckily for us, though, there are programs that allow us to cut through this confusion and see the various programs that are automatically starting when windows boots. The program we recommend for this, because its free and detailed, is Autoruns from Sysinternals. When you run this program it will list all the various programs that start when your computer is booted into Windows. For the most part, the majority of these programs are safe and should be left alone unless you know what you are doing or know you do not need them to run at startup. At this point, you should download Autoruns and try it out. Just run the Autoruns.exe and look at all the programs that start automatically. Don't uncheck or delete anything at this point. Just examine the information to see an overview of the amount of programs that are starting automatically. When you feel comfortable with what you are seeing, move on to the next section. | |
Posted on
by
j lo,
under
general info.,
knowledge database,
open discussions,
tutorials.
0
comments.
![]()
Secret Game sa MS Excel..
| Excel 2002 (Excel 10) The word on the street is that Excel 2002 does not contain an easter egg. Apparently, Microsoft has received complaints about the waste of resources and file bloat. Microsoft Web Components Now this one is very cool! Technically, it's the easter egg for the Microsoft Web Components, but you access it from an Excel workbook saved as an interactive web page. Requires Excel 2000, the Microsoft Web components, and DirectX. Open a new Excel workbook. Select File * Save as Web Page In the Save As dialog, select 'Publish Sheet' and 'Add Interactivity' Save to an htm file on your hard drive (any file name). Open the htm file with Internet Explorer 5. Select cell WC2000 and scroll the sheet such that cell WC2000 is the first cell on the left. Highlight the entire row. Press Shift+Crtl+Alt and click the Office logo in the upper-left. Your screen will be transformed into an auto racing game, with developer credits (and other things) visible on the roadway. Use the following keys: Arrow keys: to steer and accelerate Space bar: To fire at other cars O: To drop an oil slicks H: To turn on your headlights | |
Posted on
by
j lo,
under
general info.,
knowledge database,
tips and trick,
tutorials.
0
comments.
![]()
Computer Acronyms and Abbreviations
ADSL - Asymmetric Digital Subscriber Line
AGP - Accelerated Graphics Port
ALI - Acer Labs, Incorporated
ALU - Arithmetic Logic Unit
AMD - Advanced Micro Devices
APC - American Power Conversion
ASCII - American Standard Code for Information Interchange
ASIC - Application Specific Integrated Circuit
ASPI - Advanced SCSI Programming Interface
AT - Advanced Technology
ATI - ATI Technologies Inc.
ATX - Advanced Technology Extended
--- B ---
BFG - BFG Technologies
BIOS - Basic Input Output System
BNC - Barrel Nut Connector
--- C ---
CAS - Column Address Signal
CD - Compact Disk
CDR - Compact Disk Recorder
CDRW - Compact Disk Re-Writer
CD-ROM - Compact Disk - Read Only Memory
CFM - Cubic Feet per Minute (ft�/min)
CMOS - Complementary Metal Oxide Semiconductor
CPU - Central Processing Unit
CTX - CTX Technology Corporation (Commited to Excellence)
--- D ---
DDR - Double Data Rate
DDR-SDRAM - Double Data Rate - Synchronous Dynamic Random Access Memory
DFI - DFI Inc. (Design for Innovation)
DIMM - Dual Inline Memory Module
DRAM - Dynamic Random Access Memory
DPI - Dots Per Inch
DSL - See ASDL
DVD - Digital Versatile Disc
DVD-RAM - Digital Versatile Disk - Random Access Memory
--- E ---
ECC - Error Correction Code
ECS - Elitegroup Computer Systems
EDO - Extended Data Out
EEPROM - Electrically Erasable Programmable Read-Only Memory
EPROM - Erasable Programmable Read-Only Memory
EVGA - EVGA Corporation
--- F ---
FC-PGA - Flip Chip Pin Grid Array
FDC - Floppy Disk Controller
FDD - Floppy Disk Drive
FPS - Frame Per Second
FPU - Floating Point Unit
FSAA - Full Screen Anti-Aliasing
FS - For Sale
FSB - Front Side Bus
--- G ---
GB - Gigabytes
GBps - Gigabytes per second or Gigabits per second
GDI - Graphical Device Interface
GHz - GigaHertz
--- H ---
HDD - Hard Disk Drive
HIS - Hightech Information System Limited
HP - Hewlett-Packard Development Company
HSF - Heatsink-Fan
--- I ---
IBM - International Business Machines Corporation
IC - Integrated Circuit
IDE - Integrated Drive Electronics
IFS- Item for Sale
IRQ - Interrupt Request
ISA - Industry Standard Architecture
ISO - International Standards Organization
--- J ---
JBL - JBL (Jame B. Lansing) Speakers
JVC - JVC Company of America
- K ---
Kbps - Kilobits Per Second
KBps - KiloBytes per second
--- L ---
LG - LG Electronics
LAN - Local Are Network
LCD - Liquid Crystal Display
LDT - Lightning Data Transport
LED - Light Emitting Diode
--- M ---
MAC - Media Access Control
MB � MotherBoard or Megabyte
MBps - Megabytes Per Second
Mbps - Megabits Per Second or Megabits Per Second
MHz - MegaHertz
MIPS - Million Instructions Per Second
MMX - Multi-Media Extensions
MSI - Micro Star International
--- N ---
NAS - Network Attached Storage
NAT - Network Address Translation
NEC - NEC Corporation
NIC - Network Interface Card
--- O ---
OC - Overclock (Over Clock)
OCZ - OCZ Technology
OEM - Original Equipment Manufacturer
--- P ---
PC - Personal Computer
PCB - Printed Circuit Board
PCI - Peripheral Component Interconnect
PDA - Personal Digital Assistant
PCMCIA - Peripheral Component Microchannel Interconnect Architecture
PGA - Professional Graphics Array
PLD - Programmable Logic Device
PM - Private Message / Private Messaging
PnP - Plug 'n Play
PNY - PNY Technology
POST - Power On Self Test
PPPoA - Point-to-Point Protocol over ATM
PPPoE - Point-to-Point Protocol over Ethernet
PQI - PQI Corporation
PSU - Power Supply Unit
--- R ---
RAID - Redundant Array of Inexpensive Disks
RAM - Random Access Memory
RAMDAC - Random Access Memory Digital Analog Convertor
RDRAM - Rambus Dynamic Random Access Memory
ROM - Read Only Memory
RPM - Revolutions Per Minute
--- S ---
SASID - Self-scanned Amorphous Silicon Integrated Display
SCA - SCSI Configured Automatically
SCSI - Small Computer System Interface
SDRAM - Synchronous Dynamic Random Access Memory
SECC - Single Edge Contact Connector
SODIMM - Small Outline Dual Inline Memory Module
SPARC - Scalable Processor ArChitecture
SOHO - Small Office Home Office
SRAM - Static Random Access Memory
SSE - Streaming SIMD Extensions
SVGA - Super Video Graphics Array
S/PDIF - Sony/Philips Digital Interface
--- T ---
TB - Terabytes
TBps - Terabytes per second
Tbps - Terabits per second
TDK - TDK Electronics
TEC - Thermoelectric Cooler
TPC - TipidPC
TWAIN - Technology Without An Important Name
--- U ---
UART - Universal Asynchronous Receiver/Transmitter
USB - Universal Serial Bus
UTP - Unshieled Twisted Pair
--- V ---
VCD - Video CD
VPN - Virtual Private Network
--- W ---
WAN - Wide Area Network
WTB - Want to Buy
WYSIWYG - What You See Is What You Get
--- X ---
XGA - Extended Graphics Array
XFX - XFX Graphics, a Division of Pine
XMS - Extended Memory Specification
XT - Extended Technology
Posted on
by
j lo,
under
general info.,
knowledge database,
tips and trick,
tutorials.
0
comments.
![]()
Make your IE works fast like Firefox
1. click start > run
2. type regedit > enter
3. browse folder HKEY_CURRENT_USER\Software\m*cro$oft\Windows\Curre ntVersion\InternetSettings
4. right click @ windows right > New > DWORD
5. type MaxConnectionsPerServer > u can set value (the more higher the no, the more good speed u get, eg : 99)
6. create another DWORD >type MaxConnectionsPer1_0Server
7. then put a high value as mentioned above
8. then, restart IE ... ur finished.
Posted on
by
j lo,
under
knowledge database,
open discussions,
tips and trick,
tutorials.
0
comments.
![]()
A Trick To Check Your Antivirus Is Working Properly
Open notepad
Copy this code in the text file....
"X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*"
without qutoes....
then save it with the name fanything.exe
If this file got deleted immediately..that means ur antivirus is working n updated..
Posted on
by
j lo,
under
security and protection,
tips and trick,
tutorials.
0
comments.
![]()
BricoPack Vista Inspirat

Description :
BricoPack Vista Inspirat is a free pack which modifies Windows XP system files in order to change its appearance and make it look like Windows Vista (the next operating system made by Microsoft).
Rewarded by a lot of magazine, Vista Inspirat BricoPack is the best way to change quickly and easily your Windows icons, logon and visual style.
Download:
here is the link: http://www.crystalxp.net/galerie/en.id.130.htm
Posted on
by
j lo,
under
software,
themes.
0
comments.
![]()
How to Enable Right Click on Sites that Disable it-OLD TRICK
There are lots of web sites that have disabled the right click function
of the mouse button... which it's really, really annoying!!
This is done so that you don't steal (via right-click->save picture) their photos
or images or any other goodies.
Unfortunately, it disables ALL right-click functionality:
copy, paste, open in new window.
But It's easy to change, assuming your using IE 6 or higher:
Click "Tools"->"Internet Options"
Click the "Security" tab
Click "Custom Level"
Scroll down to the "Scripting" section
Set "Active Scripting" to "disable"
Click "Ok" a couple of times.
You'll probably want to turn this back to "enable" when your done,
'cause generally the java script enhances a website
or in firefox..
tools->options->content..
turn off java and javascript, then reload the site.
ALTERNATIVELY:
Before you change settings try holding down the Ctrl key and right clicking.
This also works in a lot of cases....
Posted on
by
j lo,
under
knowledge database,
tips and trick,
troubleshooting,
tutorials.
0
comments.
![]()
How to Block or Unblock a Website?
Just Follow this step..
Open C:\Windows\system32\drivers
There you will find a file named"HOSTS"..
Right-click on it
Select open
then choose Notepad then ok.
Now,in the file under the line 127.0.0.1 localhost
Add another line as 127.0.0.2 www.friendster.com (the website that i want to block)
Then save your work..
And visit the site that you blocked!!
Posted on
by
j lo,
under
knowledge database,
tips and trick,
troubleshooting,
tutorials.
0
comments.
![]()
138 Commands of Command Prompt ( DOS ) with description
| 1 ANSI.SYS -- Defines functions that change display graphics, control cursor movement, and reassign keys. 2 APPEND -- Causes MS-DOS to look in other directories when editing a file or running a command. 3 ARP -- Displays, adds, and removes arp information from network devices 4 ASSIGN -- Assign a drive letter to an alternate letter 5 ASSOC -- View the file associations 6 AT -- Schedule a time to execute commands or programs. 7 ATMADM -- Lists connections and addresses seen by Windows ATM call manager. 8 ATTRIB -- Display and change file attributes. 9 BATCH -- NRecovery console command that executes a series of commands in a file. 10 BOOTCFG -- Recovery console command that allows a user to view, modify, and rebuild the boot.ini 11 BREAK -- Enable / disable CTRL + C feature. 12 CACLS -- View and modify file ACL's. 13 CALL -- Calls a batch file from another batch file. 14 CD -- Changes directories. 15 CHCP -- Supplement the International keyboard and character set information. 16 CHDIR -- Changes directories. 17 CHKDSK -- Check the hard disk drive running FAT for errors. 18 CHKNTFS -- Check the hard disk drive running NTFS for errors. 19 CHOICE -- Specify a listing of multiple options within a batch file. 20 CLS -- Clears the screen. 21 CMD -- Opens the command interpreter. 22 COLOR -- Easily change the foreground and background color of the MS-DOS window. 23 COMP -- Compares files. 24 COMPACT -- Compresses and uncompress files. 25 CONTROL -- Open control panel icons from the MS-DOS prompt. 26 CONVERT Convert FAT to NTFS. 27 COPY -- Copy one or more files to an alternate location. 28 CTTY -- Change the computers input/output devices. 29 DATE -- View or change the systems date. 30 DEBUG -- Debug utility to create assembly programs to modify hardware settings. 31 DEFRAG -- Re-arrange the hard disk drive to help with loading programs. 32 DEL -- Deletes one or more files. 33 DELETE -- Recovery console command that deletes a file. 34 DELTREE -- Deletes one or more files and/or directories. 35 DIR -- List the contents of one or more directory. 36 DISABLE -- Recovery console command that disables Windows system services or drivers. 37 DISKCOMP -- Compare a disk with another disk. 38 DISKCOPY -- Copy the contents of one disk and place them on another disk. 39 DOSKEY -- Command to view and execute commands that have been run in the past. 40 DOSSHELL -- A GUI to help with early MS-DOS users. 41 DRIVPARM -- Enables overwrite of original device drivers. 42 ECHO -- Displays messages and enables and disables echo. 43 EDIT -- View and edit files. 44 EDLIN -- View and edit files. 45 EMM386 -- Load extended Memory Manager. 46 ENABLE -- Recovery console command to enable a disable service or driver. 47 ENDLOCAL -- Stops the localization of the environment changes enabled by the setlocal command. 48 ERASE -- Erase files from computer. 49 EXPAND -- Expand a Microsoft Windows file back to it's original format. 50 EXIT -- Exit from the command interpreter. 51 EXTRACT -- Extract files from the Microsoft Windows cabinets. 52 FASTHELP -- Displays a listing of MS-DOS commands and information about them 53 FC -- Compare files. 54 FDISK -- Utility used to create partitions on the hard disk drive. 55 FIND -- Search for text within a file. 56 FINDSTR -- Searches for a string of text within a file. 57 FIXBOOT -- Writes a new boot sector. 59 FIXMBR -- Writes a new boot record to a disk drive. 60 FOR -- Boolean used in batch files. 61 FORMAT -- Command to erase and prepare a disk drive. 62 FTP -- Command to connect and operate on a FTP server. 63 FTYPE -- Displays or modifies file types used in file extension associations. 64 GOTO -- Moves a batch file to a specific label or location. 65 GRAFTABL -- Show extended characters in graphics mode. 66 HELP -- Display a listing of commands and brief explanation. 67 IF -- Allows for batch files to perform conditional processing. 68 IFSHLP.SYS -- 32-bit file manager. 69 IPCONFIG -- Network command to view network adapter settings and assigned values. 70 KEYB -- Change layout of keyboard. 71 LABEL -- Change the label of a disk drive. 72 LH -- Load a device driver in to high memory. 73 LISTSVC -- Recovery console command that displays the services and drivers. 74 LOADFIX -- Load a program above the first 64k. 75 LOADHIGH -- Load a device driver in to high memory. 76 LOCK -- Lock the hard disk drive. 77 LOGON -- Recovery console command to list installations and enable administrator login. 78 MAP -- Displays the device name of a drive. 79 MD -- Command to create a new directory. 80 MEM -- Display memory on system. 81 MKDIR -- Command to create a new directory. 82 MODE -- Modify the port or display settings. 83 MORE -- Display one page at a time. 84 MOVE -- Move one or more files from one directory to another DIRECTORY 85 MSAV -- Early Microsoft Virus scanner. 86 MSD -- Diagnostics utility. 87 MSCDEX -- Utility used to load and provide access to the CD-ROM. 88 NBTSTAT -- Displays protocol statistics and current TCP/IP connections using NBT 89 NET -- Update, fix, or view the network or network settings 90 NETSH -- Configure dynamic and static network information from MS-DOS. 91 NETSTAT -- Display the TCP/IP network protocol statistics and information. 92 NLSFUNC -- Load country specific information. 93 NSLOOKUP -- Look up an IP address of a domain or host on a network. 94 PATH -- View and modify the computers path location 95 PATHPING -- View and locate locations of network latency 96 PAUSE -- command used in batch files to stop the processing of a command. 97 PING -- Test / send information to another network computer or network device . 98 POPD -- Changes to the directory or network path stored by the pushd command. 99 POWER -- Conserve power with computer portables. 100 PRINT -- Prints data to a printer port. 101 PROMPT -- View and change the MS-DOS prompt. 102 PUSHD -- Stores a directory or network path in memory so it can be returned to at any time. 103 QBASIC -- Open the QBasic. 104 RD -- Removes an empty directory. 105 REN -- Renames a file or directory. 106 RENAME -- Renames a file or directory. 107 RMDIR -- Removes an empty directory. 108 ROUTE -- View and configure windows network route tables. 109 RUNAS -- Enables a user to execute a program on another computer. 110 SCANDISK -- Run the scandisk utility. 111 SCANREG -- Scan registry and recover registry from errors. 112 SET -- Change one variable or string to another. 113 SETLOCAL -- Enables local environments to be changed without affecting anything else. 114 SHARE -- Installs support for file sharing and locking capabilities. 115 SETVER -- Change MS-DOS version to trick older MS-DOS programs. 116 SHIFT -- Changes the position of replaceable parameters in a batch program. 117 SHUTDOWN -- Shutdown the computer from the MS-DOS prompt. 118 SMARTDRV -- Create a disk cache in conventional memory or extended memory. 119 SORT -- Sorts the input and displays the output to the screen. 120 START -- Start a separate window in Windows from the MS-DOS prompt. 121 SUBST -- Substitute a folder on your computer for another drive letter. 122 SWITCHES -- Remove add functions from MS-DOS. 123 SYS -- Transfer system files to disk drive. 124 TELNET -- Telnet to another computer / device from the prompt. 125 TIME -- View or modify the system time. 126 TITLE -- Change the title of their MS-DOS window. 127 TRACERT -- Visually view a network packets route across a network. 128 TREE -- View a visual tree of the hard disk drive. 129 TYPE -- Display the contents of a file. 130 UNDELETE -- Undelete a file that has been deleted. 131 UNFORMAT -- Unformat a hard disk drive. 132 UNLOCK -- Unlock a disk drive. 133 VER -- Display the version information. 134 VERIFY -- Enables or disables the feature to determine if files have been written properly. 135 VOL -- Displays the volume information about the designated drive. 136 XCOPY -- Copy multiple files, directories, and/or drives from one location to another. 137 TRUENAME -- When placed before a file, will display the whole directory in which it exists 138 TASKKILL -- It allows you to kill those unneeded or locked up applications | |
Posted on
by
j lo,
under
knowledge database,
open discussions,
tips and trick,
tutorials.
0
comments.
![]()
Common Troubleshooting Techniques & Strategies
Here are five common-sense techniques and strategies to solve common computer hardware problems.
(1) Trial-and-error
Personal computers are highly modular by design. The most powerful trouble-shooting technique is to isolate the problem to a specific component by trial-and-error. Swap compatible components and see if the system still works. Try different peripherals on different machines and see if the same problem occurs. Make one change at a time.
(2) "It's the cable, s-----."
More than 70% of all computer problems are related to cabling and connections. Ensure all cables are connected firmly. IDE and floppy ribbon cables and power cables can often go loose. Ensure microprocessor, memory modules, and adapters such as video card and sound card are inserted correctly and didn't "pop-up" during transportation.
(3) Don't be frustrated!
Don't be afraid of computer problems. It is often the best opportunity to learn. Trouble-shooting is part of the fun of owning a computer. Imagine the satisfaction you could get by solving a problem yourself.
Of course the fun could ran out quickly once you are frustrated and have spent too much time on the same problem. If you feel frustrated, it's time to leave it for a while and go back with some new ideas or call someone who can help. Rule of thumb: You shouldn't spend more than three hours on the same problem at one time.
(4) Take notes!
Take notes of what you have done and all the error messages. You may need to use them later. For instance, when you see an unusual blue screen with an error message, copy the entire message onto a piece of paper. In many situations, that message may point to the right direction in getting the problem solved quickly.
(5) Take a look?
It's OK to open a computer case and take a look inside. There is only 5V and 12V DC voltage supplied to the components outside the power supply. Those who have never seen the inside of a computer are often amazed by how simple it looks. Of course, still always power down and unplug the power cord first. ![]()
Posted on
by
j lo,
under
knowledge database,
open discussions,
tips and trick,
troubleshooting.
0
comments.
![]()
Few steps to make your firefox run at lightining speed
These are few steps to make your firefox run at lightining speed.
1. First in the URL bar, Type “about:config”. This will bring up a list of commands and variables you can edit.
2. The second step is to put “network.http.pipelining” in the filter and change the value to “true”.
3. After that you will want to put “network.http.proxy.pipelining” in the filter.
Like the last one, make that value set to “true” also.
4. Next, locate “network.http.pipelining.maxrequests” and change the value to some number higher, say 10,20 or even 30, it would make up to 10,20 or 30 requests at once.
5. The last step is to right click anywhere and select “New” then “Integer”. Name it “nglayout.initialpaint.delay” and make its value “0″. This will make the browser respond faster on the information of the websites it receives.
6. Close out FireFox (make sure FireFox is closed by viewing the Task Manager) and restart it and enjoy the new mega spee.
Posted on
by
j lo,
under
knowledge database,
tips and trick,
tutorials.
0
comments.
![]()
How to stop deepfreeze!
Download This Prog : Procexp
1. Download it
2. run
3.you see Deepfreze
4.make it Suspend
5 and then deepfreeze will stop
6. have Fun
7.this program work and also stop the minute in Tinasoft etc... in cafe softwares..
Download:
here is the link:
Posted on
by
j lo,
under
security and protection,
tips and trick,
troubleshooting,
tutorials.
1 comments.
![]()
The 81st Academy Awards winners
The 81st Academy Awards ceremony was held by the Academy of Motion Picture Arts and Sciences to honor its selection of the best films of 2008 on Sunday, February 22, 2009, at the Kodak Theatre in Los Angeles, California. Australian performer Hugh Jackman hosted the ceremony for the first time.
Slumdog ended up with eight Oscars in all, including Best Picture and Best Director for Danny Boyle. In the acting categories, Kate Winslet won Best Actress for The Reader, her first win after six nominations, while Sean Penn's performance in Milk netted him his second Best Actor statue. As expected, Heath Ledger was honored posthumously as Best Supporting Actor for his iconic role as the Joker in The Dark Knight; Penelope Cruz won her first Oscar as Best Supporting Actress for Vicky Cristina Barcelona, her second nomination.
Here are the 2009 Academy Award Winners:
BEST PICTURE
Slumdog Millionaire
BEST DIRECTOR
Danny Boyle, Slumdog Millionaire
BEST ACTOR
Sean Penn, Milk
BEST ACTRESS
Kate Winslet, The Reader
BEST SUPPORTING ACTOR
Heath Ledger, The Dark Knight
BEST SUPPORTING ACTRESS
Penélope Cruz, Vicky Cristina Barcelona
BEST ORIGINAL SCREENPLAY
Milk, Dustin Lance Black
BEST ADAPTED SCREENPLAY
Slumdog Millionaire, Simon Beaufoy
BEST ANIMATED FEATURE
WALL-E
BEST ANIMATED SHORT
La Maison en Petits Cubes
BEST ART DIRECTION
The Curious Case of Benjamin Button
BEST CINEMATOGRAPHY
Slumdog Millionaire
BEST COSTUME DESIGN
The Duchess
BEST DOCUMENTARY FEATURE
Man on Wire
BEST DOCUMENTARY SHORT
Smile Pinki
BEST EDITING
Slumdog Millionaire
BEST FOREIGN LANGUAGE FILM
Departures (Japan)
BEST LIVE ACTION SHORT
Spielzeugland (Toyland)
BEST MAKEUP
The Curious Case of Benjamin Button
BEST ORIGINAL SCORE
Slumdog Millionaire, A.R. Rahman
BEST ORIGINAL SONG
''Jai Ho,'' Slumdog Millionaire
BEST SOUND EDITING
The Dark Knight
BEST SOUND MIXING
Slumdog Millionaire
BEST VISUAL EFFECTS
The Curious Case of Benjamin Button
Posted on
by
j lo,
under
events,
movie.
0
comments.
![]()
MYX music awards 2009 winners
 The recent annual MYX Music Awards 2009 boasted of bringing together the biggest names in the music industry with the presence of performers, presenters and awardees. The night was undoubtedly another huge success for the country’s number one music channel, MYX.
The recent annual MYX Music Awards 2009 boasted of bringing together the biggest names in the music industry with the presence of performers, presenters and awardees. The night was undoubtedly another huge success for the country’s number one music channel, MYX.
Here are the 2009 MYX Music Awards winners:
Favorite Myx Bandarito Performance: Astrojuan
Favorite Myx Live Performance: Imago
Favorite International Music Video: Crush by David Archuleta
Favorite Myx Celebrity VJ: Sarah Geronimo
Favorite Media Soundtrack: A Very Special Love by Sarah Geronimo
Favorite Remake: A Very Special Love by Sarah Geronimo
Favorite Collaboration: Christian Bautista and Sitti (Captured)
Favorite Guest Appearance In A Music Video: Karylle (Only Hope by Gary Valenciano)
Favorite Indie Artist: Paraluman
Favorite New Artist: Rico Blanco
Favorite Mellow Video: A Very Special Love by Sarah Geronimo
Favorite Rock Video: Ang Pusa Mo by Pedicab
Favorite Urban Video: Shake that thing by Dannie Boi featuring Beatmox
Favorite Group: 6cyclemind
Favorite Male Artist: Erik Santos
Favorite Female Artist: Sarah Geronimo
Favorite Artist: Sarah Geronimo
Favorite Song: Betamax by Sandwich
Favorite Music Video: Procrastinator by Sandwich
Catch the premiere airing date of the 4th MYX Music Awards on March 1, Sunday with its complete coverage starting at 8:30pm with the Red Carpet Special, 9:00pm for the MYX Music Awards 2009 and at 11:30pm for the post event and after party.
Posted on
by
j lo,
under
music,
news.
0
comments.
![]()
Barkley not worried about brief upcoming jail time
Charles Barkley says he's not worried about serving a brief jail sentence after pleading guilty Monday to charges of driving drunk.
The 45-year-old former NBA star pleaded guilty to two misdemeanor charges stemming from his arrest in late December in Arizona. He's set to begin a five-day sentence March 21.
"I always knew I'd have to do time," he told The Associated Press on Wednesday. "It's not something I'm worried about."
The Hall of Famer must pay more than $2,000 in fines and attend an alcohol treatment program. Under Arizona law, he'll also be forced to install an ignition interlock device on his vehicles.
"I'm not even thinking about it," he said of the jail sentence. "When it happens, it happens."
Barkley was stopped by police Dec. 31 shortly after leaving a Scottsdale nightclub. He was arrested after failing a field sobriety test. He had a blood-alcohol level of .149 percent, nearly twice the legal limit of .08 percent in Arizona.
After a six-week leave of absence, Barkley resumed his studio analyst role for TNT last week.
The latest development in Barkley's legal woes came as he is promoting a new television series on Golf Channel called "The Haney Project," in which renowned coach Hank Haney tries to help him improve his swing.
"I made a mistake and just have to take the beatdown," Barkley said. "It is what it is. It's 100 percent my fault."
Posted on
by
j lo,
under
latest headlines in sports.
0
comments.
![]()
Barkley not worried about brief upcoming jail time
Charles Barkley says he's not worried about serving a brief jail sentence after pleading guilty Monday to charges of driving drunk.
The 45-year-old former NBA star pleaded guilty to two misdemeanor charges stemming from his arrest in late December in Arizona. He's set to begin a five-day sentence March 21.
"I always knew I'd have to do time," he told The Associated Press on Wednesday. "It's not something I'm worried about."
The Hall of Famer must pay more than $2,000 in fines and attend an alcohol treatment program. Under Arizona law, he'll also be forced to install an ignition interlock device on his vehicles.
"I'm not even thinking about it," he said of the jail sentence. "When it happens, it happens."
Barkley was stopped by police Dec. 31 shortly after leaving a Scottsdale nightclub. He was arrested after failing a field sobriety test. He had a blood-alcohol level of .149 percent, nearly twice the legal limit of .08 percent in Arizona.
After a six-week leave of absence, Barkley resumed his studio analyst role for TNT last week.
The latest development in Barkley's legal woes came as he is promoting a new television series on Golf Channel called "The Haney Project," in which renowned coach Hank Haney tries to help him improve his swing.
"I made a mistake and just have to take the beatdown," Barkley said. "It is what it is. It's 100 percent my fault."
Posted on
by
j lo,
under
latest headlines in sports.
0
comments.
![]()
Ad-Aware 2008 Professional
Ad-Aware 2008 Professional v7.1.0.8 | 19 MB
Ad-Aware 2008 is the latest version of Lavasoft??s industry leading anti-spyware solutions. Ad-Aware 2008 allows you to combat the growing threats and latest advancements of malicious spyware and malware.
Ad-Aware 2008 protects you from spyware that secretly takes control of your computer, resulting in aggressive advertising pop-ups, sluggish computer activity and even identity theft through stolen private information. We give you the tools to detect hazardous content on your computer, clearly identify their threat level, and then give you the control to remove unwanted content, so that your private information remains right where it should - under your control.
Ad-Aware Pro offers advanced features for savvy computer users and IT professionals - for optimal control of confidential information and protection against malware attacks - with detection, cleanup, and removal in one easy-to-use program
Download:
here is the link: http://rapidshare.com/files/116961758/A.d-A.w.a.r.e.2008.Pro-v7.1.0.8.rar
enjoy!
Posted on
by
j lo,
under
security and protection,
software.
1 comments.
![]()
Difference Between LOVE and CRUSH
Try to say this to the one you adore,
"I love you"
It is ok to say it, right? But how about this,
"I crush you"
You sound like you’re going to kill him.
So they differ a lot. 
Posted on
by
j lo,
under
love.
1 comments.
![]()
The TEN Commandments
These are the Commandments which God gave to man to guide him to happiness in this life and in the next:
1. I AM THE LORD THY GOD: THOU SHALT NOT HAVE STRANGE GODS BEFORE ME.
Commands: faith, hope, love and worship of God, reverence for holy things, prayer.
Forbids: idolatry, superstition; spiritualism, seances, astrology, fortune telling, ouija boards and all occult practices; tempting God, sacrilege, attendance at false worship.
2. THOU SHALT NOT TAKE THE NAME OF THE LORD THY GOD IN VAIN.
Commands: reverence in speaking about God and holy things; the keeping of oaths and vows.
Forbids: blasphemy, the irreverent use of God’s name, speaking disrespectfully of holy things, false oaths and the breaking of vows.
3. REMEMBER THOU KEEP HOLY THE SABBATH DAY.
Commands: going to Church on Sundays and Holy Days.
Forbids: missing Church through one’s own fault; unnecessary servile work; public buying and selling; court trials.
4. HONOR THY FATHER AND MOTHER.
Commands: love, respect, obedience on the part of children; care on the part of parents for the spiritual and temporal welfare of their children; obedience to civil and religious superiors.
Forbids: hatred of parents and superiors; disrespect and disobedience.
5. THOU SHALL NOT KILL.
Commands: safeguarding of one’s own life and bodily welfare of that of others; controlling one’s anger.
Forbids: unjust killing, suicide, abortion, euthanasia, artificial contraception, sterilization, fist fights, endangering life and limb of self or others.
6. THOU SHALT NOT COMMIT ADULTERY.
Commands: chastity in word and deed; avoiding occasions of sin.
Forbids: pornography, bad movies, obscene speech; impure actions alone or with others; masturbation, fornication, homosexuality, incest, bestiality.
7. THOU SHALT NOT STEAL.
Commands: respect for the property and rights of others; the paying of just debts; paying just wages to employees; integrity in public officials.
Forbids: theft; damage to the property of others; not paying just debts; not returning found or borrowed articles; giving unjust measure or weight in selling; not paying just wages; bribery; graft; cheating; fraud; accepting stolen property; not giving an honest day’s work for wages received; violation of contract.
8. THOU SHALT NOT BEAR FALSE WITNESS AGAINST THY NEIGHBOR.
Commands: truthfulness, respect for the good name of other; the observance of secrecy when required.
Forbids: lying, injury to good name of others, slander, tale bearing, rash judgement, contemptuous speech; and the violation of secrecy.
9. THOU SHALT NOT COVET THY NEIGHBOR’S WIFE.
Commands: purity in thought.
Forbids: willful impure thoughts and desires.
10. THOU SHALT NOT COVET THY NEIGHBOR’S GOODS.
Commands: respect for the rights of others.
Forbids: the desire to take, to keep, or to damage the property of others.
Posted on
by
j lo,
under
religious talk.
0
comments.
![]()
How to Remove the "Run" Command from the Start Menu. In windows Xp.
Configuring a computer for a tech novice and don't want them accidentally poking around the internals? One way to help prevent them from trying to run software they weren't meant to execute is to disable the "Run" command from the Windows XP Start Menu.
1. Right-click the "Start" button, selecting "Properties".
2. When the "Taskbar and Start Menu Properties" multi-tabbed dialog box appears, click the "Start Menu" tab if it is not already selected.
3. Click the "Start Menu" radio button (if it is not already selected) and click "Customize".
4. When the "Customize Start Menu" dialog box appears, click the "Advanced" tab.
5. Underneath "Start menu items", scroll down to "Run command" and uncheck it.
6. Click "OK" on the dialog boxes to close them.
Note that this will not completely secure a system from those who know what they are doing. Making this change will not prevent users from going through the above steps and re-adding the "Run" command, nor will it prevent them from running software via the Windows Task Manager's "File" - "New Task (Run") option. However, this may prevent some computer neophytes from executing software that could damage their system.
Posted on
by
j lo,
under
tips and trick,
troubleshooting,
tutorials.
0
comments.
![]()
How to disable the "right click" of the mouse using regedit in windows XP
You can disable the right-click feature on your mouse in only a few minutes. Once the following steps are completed, your mouse will no longer be able to access the context menu for desktop or Windows Explorer in the usual way. This method will disable the right-click function for your desktop and Explorer only.
Instructions:
Step1
Click on "Start" and select "Run." Type "regedit" into the textbox and hit "OK." This command will open the "Registry Editor" window.
Step2
Select "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer."
Step3
Open the "Edit" menu and choose "New" then "DWORD Value." A new file will appear on the right side of your screen with the file name highlighted. Type in "NoViewContextMenu" for the new file name.
Step4
Double click to open and type in "0" into the Value data box. Hit the "OK" button.
Step5
Close the Registry Editor by selecting "Exit" from the "File" menu. Restart your computer for the change to go into effect and you have now disabled your right-click feature.
Tips & Warnings
* The change will affect only the current user. To disable for all users instead of selecting "HKEY_CURRENT_USER," choose "HKEY_LOCAL_MACHINE" and continue with the above path.
* If you wish to re-enable the right-click feature, return to the "NoViewContextMenu" and change the Value data box to "1". Restart your computer.
* This change should only be performed by individuals familiar with the registry editor.
Posted on
by
j lo,
under
tips and trick,
troubleshooting,
tutorials.
0
comments.
![]()
February 20-23, 2009 TNS Nationwide Ratings: Primetime Bida rules nationwide
 Here are the comparative TV ratings of ABS-CBN and GMA-7 programs from February 20 to 23 based on the overnight ratings of Taylor Nelson Sofres (TNS) among National households:
Here are the comparative TV ratings of ABS-CBN and GMA-7 programs from February 20 to 23 based on the overnight ratings of Taylor Nelson Sofres (TNS) among National households:
February 20, Friday
Non-Primetime:
Ruffa and Ai (ABS-CBN) 9.2%; SiS (GMA-7) 8.6%
Pilipinas, Game KNB? (ABS-CBN) 17.3%; Lalola (GMA-7) 12%
Wowowee (ABS-CBN) 21.5%; Eat Bulaga! (GMA-7) 16.4%
Parekoy (ABS-CBN) 16%; Daisy Siete (GMA-7) 16.7%
Pieta (ABS-CBN) 17.4%; Paano Ba ang Mangarap? (GMA-7) 19%
La Traicion (ABS-CBN) 12.3%; Saan Darating ang Umaga? (GMA-7) 21.3%
Mr. Bean Live (ABS-CBN) 10.8%; Be Strong Geum Soon (GMA-7) 12.2%
Mischievous Princess (ABS-CBN) 12%; Love at the Corner (GMA-7) 10.3%
Primetime:
Kapamilya, Deal Or No Deal (ABS-CBN) 18.9%; Family Feud (GMA-7) 14.9%
TV Patrol World (ABS-CBN) 33%; 24 Oras (GMA-7) 22.2%
May Bukas Pa (ABS-CBN) 40.5%; Luna Mystika (GMA-7) 28.7%; I Love Betty La Fea (ABS-CBN) 38.5%
Tayong Dalawa (ABS-CBN) 38.9%; Gagambino (GMA-7) 28.5%
SNN: Showbiz News Ngayon (ABS-CBN) 27.1%; Ang Babaeng Hinugot Sa Aking Tadyang (GMA-7) 24.2%
Pinoy Fear Factor (ABS-CBN) 23.4%; Fated To Love You (GMA-7) 19.8%
February 21, Saturday
Non-Primetime:
Lovely Day (GMA-7) 9.6%; Pilipinas, Game KNB? (ABS-CBN) 11.9%; Maynila (GMA-7) 9.5%
Wowowee (ABS-CBN) 21.9%; Takeshi's Castle (GMA-7) 12.3%; Eat Bulaga! (GMA-7) 17.3%
Entertainment Live (ABS-CBN) 10.4%; Startalk (GMA-7) 9.6%
Cinema FPJ: Da King on ABS-CBN (ABS-CBN) 16.6%; Wish Ko Lang (GMA-7) 10.4%
Komiks Presents Flash Bomba (ABS-CBN) 20.3%; Pinoy Records (GMA-7) 11.6%
Primetime:
The Singing Bee (ABS-CBN) 26.5%; Kakasa Ka Ba Sa Grade 5? (GMA-7) 15.8%
Maalaala Mo Kaya (ABS-CBN) 34.4%; Bitoy's Funniest Videos (GMA-7) 21.2%; Kapuso Mo Jessica Soho (GMA-7) 21.6%
Banana Split (ABS-CBN) 17.6%; Imbestigador (GMA-7) 21.8%
XXX (ABS-CBN) 10.9%; Kapuso Movie Festival (ABS-CBN) 13.6%
February 22, Sunday
Non-Primetime:
Matanglawin (ABS-CBN) 12.3%; Takeshi's Castle (GMA-7) 10%
ASAP '09 (ABS-CBN) 17.9%; SOP (GMA-7) 13.1%
Your Song (ABS-CBN) 13.1%; Dear Friend (GMA-7) 10.7%
The Buzz (ABS-CBN) 11.7%; Showbiz Central (GMA-7) 11.1%
Primetime:
Goin' Bulilit (ABS-CBN) 19.7%; The Singing Bee (ABS-CBN) 26.2%; Kap's Amazing Stories (GMA-7) 23.3%
Rated K (ABS-CBN) 31.1%; My Dad Is Better Than Your Dad (GMA-7) 20.9%; Mel & Joey (GMA-7) 19.9%
Sharon (ABS-CBN) 23.2%; All Star K (GMA-7) 16.5%
TV Patrol Linggo (ABS-CBN) 17.5%; Ful Haus (GMA-7) 15.1%
Sunday's Best (ABS-CBN) 5.1%; SNBO (GMA-7) 10.5%
February 23, Monday
Non-Primetime:
Mr. Bean (ABS-CBN) 10.2%; Ruffa and Ai (ABS-CBN) 9.2%; Doraemon (GMA-7) 14.3%; Pokemon (GMA-7) 16.4%; Slamdunk (GMA-7) 15.7%
81st Oscar Awards (ABS-CBN) 13%; Bleach (GMA-7) 11%; SiS (GMA-7) 9%; Lalola (GMA-7) 11.7%
Wowowee (ABS-CBN) 19.4%; Eat Bulaga! (GMA-7) 20.4%
Parekoy (ABS-CBN) 16.3%; Daisy Siete (GMA-7) 16.4%
Pieta (ABS-CBN) 15%; Paano Ba ang Mangarap? (GMA-7) 18.8%
La Traicion (ABS-CBN) 12.7%; Saan Darating ang Umaga? (GMA-7) 19.9%
Mischievous Princess (ABS-CBN) 11.7%; Be Strong Geum Soon (GMA-7) 11.9%; Love at the Corner (GMA-7) 9.5%
Primetime:
Kapamilya, Deal Or No Deal (ABS-CBN) 17.5%; Family Feud (GMA-7) 14.4%
TV Patrol World (ABS-CBN) 31.2%; 24 Oras (GMA-7) 23.8%
May Bukas Pa (ABS-CBN) 39.7%; Luna Mystika (GMA-7) 28.2%; I Love Betty La Fea (ABS-CBN) 37%
Tayong Dalawa (ABS-CBN) 32.7%; Totoy Bato (GMA-7) 30.9%
SNN: Showbiz News Ngayon (ABS-CBN) 20.6%; Ang Babaeng Hinugot Sa Aking Tadyang (GMA-7) 23.1%
Bandila (ABS-CBN) 8.6%; Fated To Love You (GMA-7) 18%
Posted on
Monday, February 23, 2009
by
j lo,
under
events,
ratings.
0
comments.
![]()
Non-scientific Answers to Questions about Love
Are your palms sweaty, is your heart racing, And your voice is caught within your chest?
-It isn't Love, it's Like.
You can't keep your eyes or hands off of them, am I right?
-It isn't Love, it's Lust.
Are you proud, and eager to show them off?
-It isn't Love, it's Luck.
Do you want them because you know they're there?
-It isn't Love, it's Loneliness.
Are you there because it's what everyone wants?
-It isn't Love, it's Loyalty.
Do you stay for their confessions of Love, because you don't want to hurt them?
-It isn't Love, it's Pity.
Are you there because they kissed you, or held your hand?
-It isn't Love, it's being Unconfident.
Do you belong to them because their sight makes your heart skip a beat?
-It isn't Love, it's Infatuation.
Do you pardon their faults because you care about them?
-It isn't Love, it's Friendship.
Do you tell them every day they are the only one you think of?
-It isn't Love, it's a Lie.
Are you willing to give all of your favorite things for their sake?
-It isn't Love, it's Charity.
Does your heart ache and break when they're sad?
-Then it's Love.
Are you attracted to others, but stay with them faithfully without regret?
-Then it's Love.
Do you accept their faults because they're a part of who they are?
-Then it's Love.
Do you cry for their pain, even when they're strong?
-Then it's Love.
Do their eyes see your true heart, and touch your soul so deeply it hurts?
-Then it's Love.
But do you stay because a blinding, incomprehensible mix of pain and elation pulls you close and holds you?
-Then it's Love.
Would you give them your heart, your life, your death?
-Then it's Love.
Now, if Love is painful, and tortures us so, why do we love?
Why is it all we search for in life?
This pain, this agony? Why is it all we long for? This torture, this powerful death of self?
Why?
Because it's Love
Posted on
Sunday, February 22, 2009
by
j lo,
under
love.
1 comments.
![]()
The Myth Of Refreshing The Desktop
| Do you refresh your desktop?". Ask this to any Windows user and 99% of them will reply with a "yes". Of course, there are various needs for refreshing the desktop but the majority of people who does it doesn't even know why he is doing it. Refreshing the desktop is perhaps the biggest computer myth among all Windows users. Every single person I have met does this or at least used to do it. It's not known who first discovered this remarkably useless trick and what he achieved from it, but it just spread. Most new users learn this trick from other new users without caring to know what it does. Some do it devotedly just because others do it, while some others have various weird explanations for it. A few of them assumes that it refreshes the RAM, while some others believe that doing it will somehow keep their PCs running smooth and easy. I have seen some users obsessed with refreshing the desktop, doing it every 30 seconds or so. They have even learnt the keyboard shortcut - F5 (just to mention, these are the people who never use keyboard shortcuts). They would press the key and wouldn't release it for a long time, sending the desktop into a frenzy of refreshes. What does a desktop refresh actually do? Refreshing the desktop simply redraws the icons on the desktop. That's it! It doesn't refreshes the RAM. It doesn't clean your PC. It doesn't refreshes your computer the way it does to you when you wake up from a nap. Refreshing the desktop has absolutely no effect on the working or performance of the computer. So why is the tool there? As I said, refresh is used to re-display or redraw the icons on the desktop. Sometimes when you bring some changes to the desktop icons, the change doesn't get reflected instantly. In such cases, refreshing the desktop becomes necessary to bring the change to effect. Say, you have the desktop icons set to arrange themselves alphabetically on your desktop. When you add a new item to the desktop, this item wouldn't get arranged alphabetically, instead it would appear at the bottom of icon list on the desktop, irrespective of it's name. Now if you refresh the desktop, all the icons would be once more arranged alphabetically and the newly added item would go to it's appropriate position. This is what refresh is for. It is to re-display the desktop. Refresh has the same function when done in explorer. Also Refresh is basically the command used to refresh/reload the video buffer(VGA memory). Sometimes the changes made in the VGA memory are not reflected to the screen properly...Refresh just corrects the prob... So, if you are in the habit of refreshing the desktop, stop it. You are just wasting your time and effort. And the next time you see a person doing it, don't forget to explain to him the futility of this action Also, during the times of windows 3.1 - win 95 it was normal for PCs to hang, crash n be restarted every now n then ! It looks like even knowledgeable ppl used the desktop refresh just to get an assurence that the OS is working n not freezed from the resulting flicker of icons. Today PCs are very stable n crash only once in a blue moon but the habit still continues, and I think for same reason , even I do it sometimes | |
Posted on
by
j lo,
under
news,
open discussions.
0
comments.
![]()
The most worst computer viruses of all time
If you haven't experienced a computer virus yet, just wait -- you probably will.
Fortunately, you missed the real heyday of computer viruses when anti-virus software wasn't very widely used, and virus attacks caused millions of dollars in damages overnight. Today's viruses can still be nightmarish, but for the average user, cleanup is considerably easier than it was just a few years ago, when the only solution in many cases was reformatting your hard drive and starting from scratch (and even that didn't do the trick sometimes).
So join me on a trip down memory lane as we revisit some of the worst viruses of all time and count our blessings that our computers are still up and running despite it all. (Though, please note, "worst" is a matter of considerable debate in the security industry, as the number of infected machines and amount of financial loss is always estimated. If you think another virus was worse than these, please post it in the comments to remind us!)
The worst viruses of all time
Brain, 1986
It all started here: Brain was the first "real" virus ever discovered, back in 1986. Brain didn't really hurt your PC, but it launched the malware industry with a bang and gave bad ideas to over 100,000 virus creators for the next 2 decades.
Michelangelo, 1991
The worst MS-DOS virus ever, Michelangelo attacked the boot sector of your hard drive and any floppy drive inserted into the computer, which caused the virus to spread rapidly. After spreading quietly for months, the virus "activated" on March 6, and promptly started destroying data on tens of thousands of computers.
Melissa, 1999
Technically a worm, Melissa (named after a stripper) collapsed entire email systems by causing computers to send mountains of messages to each other. The author of the virus was eventually caught and sentenced to 20 months in prison.
ILOVEYOU, 2000
This was notable for being one of the first viruses to trick users into opening a file, which in this case claimed to be a love letter sent to the recipient. In reality, the file was a VBS script that sent mountains of junk mail and deleted thousands of files. The results were terribly devastating- one estimate holds that 10 percent of all computers were affected, to a cost of $5.5 billion. It remains perhaps the worst worm of all time.
Code Red, 2001
An early "blended threat" attack, Code Red targeted Web servers instead of user machines, defacing websites and later launching denial-of-service attacks on a host of IP addresses, including those of the White House.
Nimda, 2001
Built on Code Red's attack system of finding multiple avenues into machines (email, websites, network connections, and others), Nimda infected both Web servers and user machines. It found paths into computers so effectively that, 22 minutes after it was released, it became the Internet's most widespread virus at the time.
Klez, 2001
An email virus, Klez pioneered spoofing the "From" field in email messages it sent, making it impossible to tell if Bill Gates did or did not really send you that information about getting free money.
Slammer, 2003
Another fast spreader, this worm infected about 75,000 systems in just 10 minutes, slowing the Internet to a crawl (much like Code Red) and shutting down thousands of websites.
MyDoom, 2004
Notable as the fastest-spreading email virus of all time, MyDoom infected computers so they would, in turn, send even more junk mail. In a strange twist, MyDoom was also used to attack the website of SCO Group, a very unpopular company that was suing other companies over its code being used in Linux distributions.
Storm, 2007
The worst recent virus, Storm spread via email spam with a fake attachment and ultimately infected up to 10 million computers, causing them to join its zombie botnet.
Thanks to Symantec for helping to compile this list.
Posted on
by
j lo,
under
news,
open discussions.
0
comments.
![]()
Top 20 Antivirus rankings. Tested using 174,770 virus sample
What is the the best Antivirus program ?
The latest test from virus.gr includes 52 different antivirus applications. They were rigorously tested using 174,770 virus samples, and the settings of each application were tweaked to ensure that they all caught maximum number of viruses (despite increasing the possibility that the the software would be more likely to return a false positive).
This is the list of the top 20 antivirus applications
1. Kaspersky version 7.0.0.43 beta - 99.23%
2. Kaspersky version 6.0.2.614 - 99.13%
3. Active Virus Shield by AOL version 6.0.0.308 - 99.13%
4. ZoneAlarm with KAV Antivirus version 7.0.337.000 - 99.13%
5. F-Secure 2007 version 7.01.128 - 98.56%
6. BitDefender Professional version 10 - 97.70%
7. BullGuard version 7.0.0.23 - 96.59%
8. Ashampoo version 1.30 - 95.80%
9. eScan version 8.0.671.1 - 94.43%
10. Nod32 version 2.70.32 - 94.00%
11. CyberScrub version 1.0 - 93.27%
12. Avast Professional version 4.7.986 - 92.82%
13. AVG Anti-Malware version 7.5.465 - 92.14%
14. F-Prot version 6.0.6.4 - 91.35%
15. McAfee Enterprise version 8.5.0i+AntiSpyware module - 90.65%
16. Panda 2007 version 2.01.00 - 90.06%
17. Norman version 5.90.37 - 88.47%
18. ArcaVir 2007 - 88.24%
19. McAfee version 11.0.213 - 86.13%
20. Norton Professional 2007 - 86.08%
Followed by:
21. Rising AV version 19.19.42 - 85.46%
22. Dr. Web version 4.33.2 - 85.09%
23. PC-Cillin 2007 version 15.00.1450 - 84.96%
24. Iolo version 1.1.8 - 83.35%
25. Virus Chaser version 5.0a - 79.51%
26. VBA32 version 3.11.4 - 77.66%
27. Sophos Sweep version 6.5.1 - 69.79%
28. ViRobot Expert version 5.0 - 69.53%
29. Antiy Ghostbusters version 5.2.1 - 65.95%
30. Zondex Guard version 5.4.2 - 63.79%
31. Vexira 2006 version 5.002.62 - 60.07%
32. V3 Internet Security version 2007.04.21.00 - 55.09%
33. Comodo version 2.0.12.47 beta - 53.94%
34. Comodo version 1.1.0.3 - 53.39%
35. A-Squared Anti-Malware version 2.1 - 52.69%
36. Ikarus version 5.19 - 50.56%
37. Digital Patrol version 5.00.37 - 49.80%
38. ClamWin version 0.90.1 - 47.95%
39. Quick Heal version 9.00 - 38.64%
40. Solo version 5.1 build 5.7.3 - 34.52%
41. Protector Plus version 8.0.A02 - 33.13%
42. PcClear version 1.0.4.3 - 27.14%
43. AntiTrojan Shield version 2.1.0.14 - 20.25%
44. PC Door Guard version 4.2.0.35- 19.95%
45. Trojan Hunter version 4.6.930 - 19.20%
46. VirIT version 6.1.75 - 18.78%
47. E-Trust PestPatrol version 8.0.0.6 - 11.80%
48. Trojan Remover version 6.6.0 - 10.44%
49. The Cleaner version 4.2.4319 - 7.26%
50. True Sword version 4.2 - 2.20%
51. Hacker Eliminator version 1.2 - 1.43%
52. Abacre version 1.4 - 0.00%
*The test was made on 23 April-10 May 2008, using Windows XP Professional SP2 on a P4 3000 Mhz, 1024MB DDRAM.
* All programs tested had the latest versions, upgrades and updates and they were tested using their full scanning capabilities e.g. heuristics, full scan etc.
*The default settings of each program were not used, in order for each program to achieve its maximum detection rate. Because of this, there is a possibility for the tested programs to detect a few false positives.
*All programs were updated on 22 April 2008, between 10.00AM and 13.00PM GMT.
*The 174770 virus samples were chosen using VS2000 according to Kaspersky, F-Prot, Nod32, Dr.Web, BitDefender and McAfee antivirus programs. Each virus sample was unique by virus name, meaning that AT LEAST 1 antivirus program detected it as a new virus.
*ALL virus samples were unpacked and the only samples that were kept were the ones that were packed using external-dos-packers (that means not winzip, winrar, winace etc).
*The virus samples had the correct file extension using a special program (Renexts) and were unique, according to checksum32 filesize.
*Most "fake" virus samples were removed, as well as "garbage" files.
*The programs MKS_VIR , PER and IPArmor were not tested because there was no english demo version available.
*The programs Anti-Hacker Expert , Command , Extendia AVK , GDATA AVK , BOClean , UNA , VET and Freedom were not tested because there was no demo version available.
*Thorough mode was not used in VBA32 due to extremely slow scan process.
*A-Squared Anti-Malware and eTrust PestPatrol are anti-trojan/anti-spyware programs, not antivirus programs
*F-Prot was tested using its command line scanner (options /adware /applications /report /streams /maxdepth=4 /heurlevel=4) because its GUI kept crashing.
*Windows Live OneCare, BKAV, PC Tools kept crashing while scanning the samples.
*TheShield uses the exact same engine as VirobotExpert.
*Avira uses the exact same engine as AntiVir.
*Fire uses the exact same engine as Solo.
*MKS_VIR uses the exact same engine as ArcaVir.
*VirusBuster uses the exact same engine as Vexira.
*BullGuard uses the exact same engine as BitDefender free edition.
*Avast Professional uses the exact same engine as Avast free edition.
*AVG Anti-Malware uses the exact same engine as AVG Antivirus free edition plus the Ewido scan engine, so it has better detection than AVG Antivirus free edition.
*A-squared Anti-Malware Professional uses the exact same engine as A-squared free edition.
* InVircible did not include a "typical" scanner-function and could not be tested.
*V-Catch checks only mail accounts and could not be tested.
*DOS-Based scanners were not tested.
*The following file types were used: SH, ELF, COM, EXE, PL, BAT, PRC, DOC, XLS, BIN, MDB, IMG, PPT, VBS, MSG, VBA, OLE, HTM, INI, SMM, TD0, REG, CLASS, HTA, JS, VI_, URL, PHP, WMF, HLP, XML, SCR, PIF, SHS, WBT, CSC, MAC, DAT, CLS, STI, INF, HQX, XMI, SIT.
Posted on
by
j lo,
under
news,
open discussions,
security and protection.
0
comments.
![]()
Intel Core i7 Extreme



Intel Corporation has launched its most advanced desktop processor ever called the Intel Core i7 processor. The first member of a new family of Nehalem processor designs, it speeds video editing, immersive games and other popular Internet and computer activities by up to 40 percent without increasing power consumption.
Intel Turbo Boost Technology automatically adjusts the clock speed of one or more of the four individual processing cores for single- and multi-threaded applications to boost performance. The Core i7 processor more than doubles the memory bandwidth of previous Intel “Extreme” platforms, speeding the transfer of computer bits and bites in and out of the processor with Intel Quickpath Technology. Intel’s Hyper-Threading Technology allows multiple computing threads to run simultaneously, effectively enabling it to do two things at once, so the Core i7 quad-core processor delivers 8-threaded performance.
Each Core i7 processor has an 8 MB level 3 cache and three channels of DDR3 1066 memory to deliver the best memory performance of any desktop platform. Intel’s top performance processor, the Intel Core i7 Extreme Edition, also removes overspeed protection, allowing further increase in the chip’s speed.
While Intel Core i7- 920 starts at $284, the top of the line Intel Core i7-965 Extreme Edition will cost $999.
Intel pointed out that when comparing Core i7 965 to a QX9770, we can get 52% more 3D gaming performance, 38% more rendering performance and 41% more movie editing and conversion performance.
Though the 965 XE is a four core processor like the QX9770, with its new hyperthreading technology, each core is capable of processing two threads simultaneously which when relatively compared to the QX9770 makes the 965 XE capable of processing double the threads as the older processor was capable of. But even though it is capable of processing double the threads, it still has the 130w heat output and thanks to Intel's new "Turbo Mode" and Power Gate features in its new SkullTrail based motherboards, the motherboard and processor can essentially turn off unneeded processors to save power and reduce heat output when they are not needed and to also reduce power leakage.
Posted on
by
j lo,
under
news,
open discussions,
processor.
0
comments.
![]()
10 new OS !!!
This post is about the desktop operating systems that fly under the radar of most people.
We are definitely not talking about Windows, Mac OS X or Linux, or even BSD or Solaris.
There are much less mainstream options out there for the OS-curious.
These alternative operating systems are usually developed either by enthusiasts or small companies (or both), and there are more of them than you might expect.
There are even more than we have included in this article, though we think this is a good selection of the more interesting ones and we have focused specifically on desktop operating systems.
As you will see, many of them are very different from what you may be used to.
We will discuss the potential of this in the conclusion of this article.
Enough introduction, let’s get started! Here is a look at 10 alternative operating systems, starting with a familiar old name…
AmigaOS 4.1
This month (September 2008) AmigaOS 4.1 was released.
Although AmigaOS is a veteran in the field (many have fond memories of the original Amiga computer), its current version is a fully modern OS.
AmigaOS only runs on specific PowerPC-based hardware platforms.
The company ACube is currently marketing and distributing AmigaOS and is going to bundle the OS with their motherboards.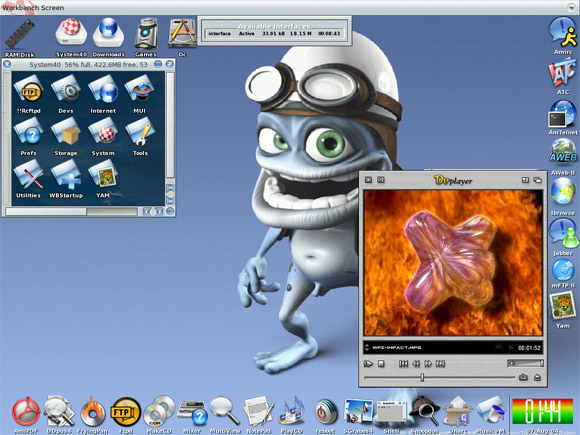
Source model: Closed source
License: Proprietary
Platform: PowerPC
State: Final
Read a review of AmigaOS 4.1 at Arstechnica
Haiku
Haiku is an open source project aimed at recreating and continuing the development of the BeOS operating system (which Palm Inc. bought and then discontinued).
Haiku was initially known as OpenBeOS but changed its name in 2004.
Haiku is compatible with software written for BeOS.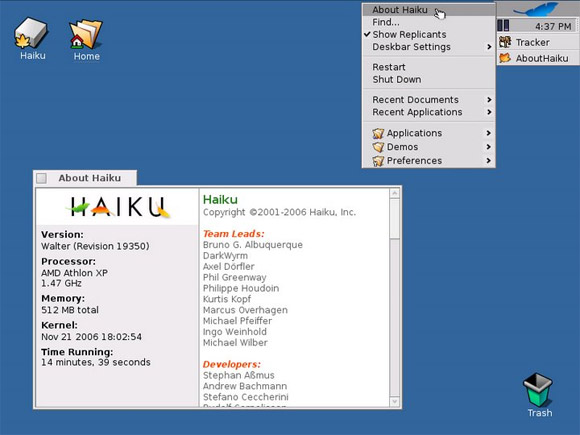
Source model: Free and open source
License: MIT License
Platform: x86 and PowerPC
State: Pre-Alpha
Read more at the Haiku website
ReactOS
ReactOS is an operating system designed to be compatible with Microsoft Windows software.
The project started in 1998 and today it can run many Windows programs well.
The ReactOS kernel has been written from scratch but the OS makes use of Wine to be able to run Windows applications.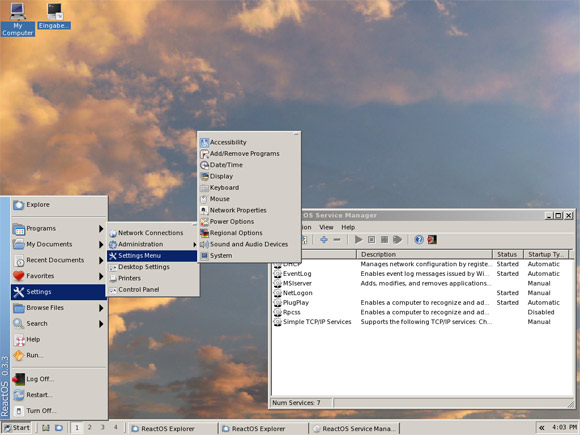
Source model: Free and open source
License: Various free software licenses
Platform: x86 (more under development)
State: Alpha
Read more at the ReactOS website.
Syllable Desktop
Syllable is a free and open source operating system that was forked in 2002 from AtheOS, an AmigaOS clone.
It’s intended as a lightweight and fast OS suitable for home and small office users.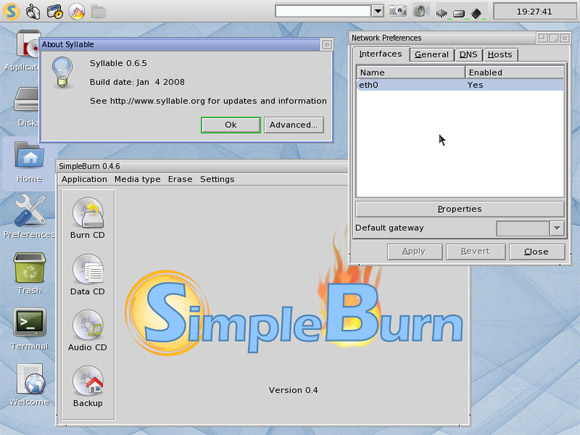
Source model: Free and open source
License: GNU General Public License
Platform: x86
State: Alpha
Read more at the Syllable website.
SkyOS
SkyOS is a closed source project written by Robert Szeleney and volunteers.
It originally started as an experiment in OS design.
It’s intended to be an easy-to-use desktop OS for average computer users.
Well-known applications such as Firefox have been ported to run on SkyOS.
Source model: Closed source
License: Proprietary
Platform: x86
State: Beta
Read more at the SkyOS website.
MorphOS
MorphOS is a lightweight, media-centric OS build to run on PowerPC processors.
It is inspired by AmigaOS and also includes emulation to be able to run Amiga applications.
Source model: Closed source
License: Mixed proprietary and open source
Platform: Pegasos, some Amiga models, EFIKA
Read more at the MorphOS website.
AROS Research Operating System
AROS is a lightweight open source OS designed to be compatible with AmigaOS 3.1 but also improve on it.
The project was started in 1995 and can today be run on both PowerPC and IBM PC compatible hardware.
It also includes an emulator that makes it possible to run old Amiga applications.
Source model: Open source
License: AROS Public License
Platform: x86 and PowerPC
Read more at the AROS website.
MenuetOS
MenuetOS, also known as MeOS, is an operating system written entirely in assembly language which makes it very small and fast.
Even though it includes a graphical desktop, networking and many other features it still fits on a single 1.44 MB floppy disk (for our younger readers, that was the USB stick of the 80s and early 90s ![]() ).
).
Source model: Open source (32-bit version), freeware (64-bit version)
License: Menuet License
Platform: x86
State: Beta
Read more at the MenuetOS website.
DexOS
DexOS is an open source operating system designed to work like the minimalistic ones on gaming consoles, but for PCs.
Its user interface is inspired by video game consoles and the system itself is very small
(supposedly this one also fits on a floppy disk, like MenuetOS) and the OS can be booted from several different devices.
Its creators have tried to make it as fast as possible.
Source model: Free and open source
Platform: x86
Read more at the DexOS website.
Visopsys
Visopsys is a one-man hobby project by programmer Andy McLaughlin.
The development began in 1997 and the OS is both open source and free.
Visopsys stands for VISual Operating SYStem.
Source model: Open source
License: GPL
Platform: x86
State: Final
Read more at the Visopsys website.
The OS future
Even if none of these operating systems ever were to “make it” and become mainstream
(and admittedly, some of them simply are not intended to be mainstream),
the passion behind them is real, and many have the potential to introduce new and fresh ideas.
All this independent development can act as a kind of think tank,
if you choose to look at it that way. It’s quite possible that concepts introduced by a niche OS will later be adopted by a larger player on the OS market.
There are lots of interesting things happening today with the rise of virtualization
and the “always online” nature of today’s computers that opens up incredibly interesting possibilities.
For example, what we have read about Microsoft’s internal research OS Midori (the one that will retire Windows) sounds highly interesting.
Wherever the future operating systems may come from, be it from the already established players
or some kind of newcomer, we are looking forward to seeing what the future has in store for us.
We suspect that there is a significant “jump” in the evolution coming up just around the corner.
Who knows, a couple of years from now maybe all the computers will be running the UltraMagicalSuperVirtualOS version 1.2?
What are your predictions for the future of operating systems?
Posted on
by
j lo,
under
open discussions,
OS.
0
comments.
![]()
openoffice.org
OpenOffice.org is a multiplatform and multilingual office suite and an open-source project. Compatible with all other major office suites, the product is free to download, use, and distribute. OpenOffice.org is sponsored by Sun Microsystems, which is the primary contributor of code to the Project. Over 180,000 people from every nearly every curve of the globe have joined this Project with the idea of creating the best possible office suite that all can use. They do so under the auspices of "open source
Download:
here is the link: http://download.openoffice.org/
Enjoy!
Posted on
by
j lo,
under
all-in-one,
software.
0
comments.
![]()
Smile muna tayo! hehhe!
He: Yes. At last. It was so hard to wait.
She: Do you want me to leave?
He: No! Don't even think about it.
She: Do you love me?
He: Of course! Over and over!
She: Have you ever cheated on me?
He: No! Why are you even asking?
She: Will you kiss me?
He: Every chance I get.
She: Will you hit me?
He: Are you crazy! I'm not that kind of person!
She: Can I trust you?
He: Yes.
She: Darling!
After marriage....
Simply read from bottom to the top.
Posted on
by
j lo,
under
jokes.
0
comments.
![]()
The creation!
I NEVER HEARD CREATION EXPLAINED THIS WAY BEFORE !!!
~
In the beginning, God created the Heavens and the Earth and populated the Earth with Broccoli, Cauliflower and Spinach, green and yellow and red Vegetables of all kinds, so Man and Woman would live Long and Healthy Lives.
~
Then using God's great gifts, Satan created Ben and Jerry's Ice Cream and Krispy Creme Donuts. And Satan said, "You want chocolate with that?" And Man said, "Yes!" and Woman said, "and as long as you're at it, add some sprinkles." And they gained 10 pounds. And Satan smiled.
~
And God created the healthful Yogurt that Woman might keep the Figure that Man found so fair.
~
And Satan brought forth white flour from the wheat, and sugar from the cane and combined them. And Woman went from size 6 to size 14.
~
So God said, "Try my fresh green salad."
~
And Satan presented Thousand-Island Dressing, buttery croutons and garlic toast on the side. And Man and Woman unfastened their belts following the repast.
~
God then said, "I have sent you heart healthy vegetables, and olive oil in which to cook them."
~
And Satan brought forth deep fried fish and chicken-fried steak so big it needed its own platter. And Man gained more weight and his cholesterol went through the roof.
~
So God then created a light, fluffy white cake, named it "Angel Food Cake," and said, "It is good."
~
Satan then created chocolate cake and named it "Devil's Food."
~
God then brought forth running shoes
so that His children might lose those extra pounds.
~
And Satan gave cable TV with
a remote control so Man would not have to toil changing the channels. And Man and Woman laughed and cried before the flickering blue light and gained pounds.
~
Then God brought forth the Potato, naturally low in fat and brimming with nutrition.
~
And Satan peeled off the healthful skin and sliced the starchy center into chips and deep-fried them. And Man gained pounds.
~
God then gave lean beef so that Man might consume fewer calories and still satisfy his appetite.
~
And Satan created McDonald's
and its 99-cent double Cheeseburger. Then said, "You want fries with that?" And Man replied, "Yes! And super size them!" And Satan said, "It is good."
~
And Man Went Into Cardiac Arrest.
~
God Sighed and Created
Quadruple Bypass Surgery.
~
Then Satan Created HMOs.
Posted on
by
j lo,
under
jokes.
0
comments.
![]()