Google Rumored To Be Breaking Up With Firefox
Are we on the verge of a new browser war?
Google is obligated to support Mozilla’s Firefox browser through a search contract until 2011. But rumors suggest that may be the end of the Google-Firefox alliance.
People were relatively stunned when Google launched its own web browser, Chrome, and they wondered allowed what that would mean for Google’s relationship with the browser that quickly rose to the second most used browser in the world.
At the height of all the Microsoft versus Google hysteria—which left us without a Microsoft contender in search and without a Google operating system—Google jumped behind Firefox, the only browser that presented a challenge to Internet Explorer since IE devastated Netscape.
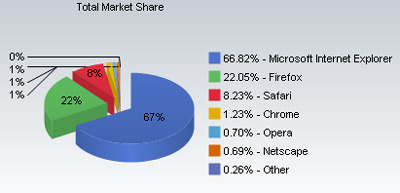
Firefox grabbed 22 percent of the browser market, helping to shrink IE’s share from 90 percent to 66 percent. Google funneled money and support to Firefox by placing invitations to download on the Google homepage, and paid about $75 million in 2007 in referrals from the Firefox search bar.
It’s that search deal that is set to expire in 2011, and according to Gawker tipsters, Google’s looking to go separate ways.
That’s bad news for Mozilla, an open source company depending on donations. Would this be an indication that Google is willing to sacrifice Firefox to the browser gods in order to boost Chrome? Well, Chrome so far still has barely cracked one percent of the market, despite being singled out as the most secure web browser by security researchers.
It could be Google feels its own browser could take Firefox’s share and a little more of IE’s if marketed properly.
source: http://www.webpronews.com
Posted on
Tuesday, April 07, 2009
by
j lo,
under
information,
news.
3
comments.
![]()
Getting More Blog Readers and Twitter Followers
Use Twitter and Blogs to Compliment Each Other
Of people who both blog and tweet, the majority would overwhelmingly prefer to have more blog readers than followers on Twitter. This is according to surveys conducted by Darren Rowse who runs ProBlogger and TwiTip.
This is not entirely surprising, since generally, much more effort is put into a blog post than a 140-character or less tweet, but there is certainly a gold-rush for Twitter followers. Jason Calacanis for one is willing to pay a pretty penny for them.
Click Here to Read More..
Posted on
by
j lo,
under
information,
news.
0
comments.
![]()
DirectX 10 for Windows Xp

Features:
DirectX 10 NCT Release 2 - this is a new patch to increase the compatibility of new games and programs with Windows XP and achieve noticeable increase in speed and quality graphics in games. The same patch corrects mistakes with the launch of games requiring files with DirectX 9.0 and earlier versions. Also, if graphics card with support for DX10 makes those options available, the next-generation games, which before the installation of these libraries were not available. In this version the number of libraries increased twice that finally allowed to reach full DirectX 10 for Windows XP.
Read more »- DirectX 10 for Windows Xp


Download link: http://ifile.it/h83neuz
Posted on
by
j lo,
under
all-in-one,
microsoft.
1 comments.
![]()
Google's Still Not Buying Twitter
Likely, Boomtown’s Kara Swisher gets tired of being the TechCrunch Google-rumor-debunker. Maybe not. She seemed to enjoy reminding readers about the Michael Arrington grapevines sprouting out tales of Google buying Digg and Bebo, neither of which ever happened. This time it’s Twitter.
In the comments of TechCrunch’s rumor report that Google was in late-stage talks to buy Twitter, Arrington notes that posting a rumor is a good way of shaking out information. Maybe next time he should just give Swisher a call and save everybody a lot of trouble. Swisher, married to a Google executive, generally has the better inside scoop.
Here’s what a Swisher source had to say about it: “Seriously, no negotiations, no deal, nada.”
That’s more in line with Google CEO Eric Schmidt’s earlier statement about sitting on Google’s money until the economy gets better. With unemployment at a predicted peak last month, that could be as early as this summer, if you’re the extra-optimistic type. Although CEOs of multinational corporations are notorious liars about everything, Schmidt’s generally made good on what he puts out to the public.
Swisher’s sources say there have been preliminary discussions between Google and Twitter about real time search and “product stuff.” That seems to match up with AdAge’s report that Google will be using Twitter to sell AdSense ads. Advertisers will have the opportunity to stream their five most recent tweets all across the AdSense network.
If Google made an offer for Twitter, an offer that would have to be near the billion-dollar range, it might be because every Tom, Dick, and Harry outside of Google really, really wants Google to buy Twitter. While Tom, Dick, (Mike) and Harry are pushing the deal, Robert Scoble reminds his audience that Google historically has been where good microblogging companies go to die.
Remember Jaiku? Dodgeball? If so, it’s only because you were aware of them before Google bought them.
source: http://www.webpronews.com
Click Here to Read More..
Posted on
by
j lo,
under
information,
news.
0
comments.
![]()
Crazy stuff
A nice story, with surprising end:
In Stuttgart, Germany, a court judge must decide on a case of honorable intentions in a situation where a man hired his neighbor to get his wife pregnant.
It seems that Demetrius Soupolos, 29, and his former beauty queen wife, Traute, wanted a child badly, but Demetrius was told by a doctor that he was sterile.
So, Soupolos, after calming his wife’s protests, hired his neighbor, Frank Maus, 34, to impregnate her. Since Maus was already married and the father of two children, plus looked very much like Soupolos to boot, the plan seemed good.
Soupolos paid Maus $2,500 for the job and for three evenings a week for the next six months, Maus tried desperately, a total of 72 different times, to impregnate Traute.
When his own wife objected, he explained, "I don’t like this any more than you. I’m simply doing it for the money. Try and understand."
When Traute failed to get pregnant after six months, however, Soupolos was not understanding and insisted that Maus have a medical examination, which he did.
The doctor’s announcement that Maus was also sterile shocked everyone except his wife, who was forced to confess that Maus was not the real father of their two children.
Now Soupolos is suing Maus for breach of contract in an effort to get his money back, but Maus refuses to give it up because he said he did not guarantee conception, but only that he would give an honest effort.
Posted on
Saturday, April 04, 2009
by
j lo,
under
funny,
jokes.
0
comments.
![]()
Avast Pro v.4.8 + lifetime patch

Avast! 4.8 Professional Edition represents the best antivirus protection available and can be downloaded and used free of charge for a 60-day trial period. At the end of the trial period, a license key must be purchased, which will be valid for a further 1, 2, or 3 years. avast! 4 Professional Edition comes with anti-spyware, anti-rootkit and strong self-protection built-in. It is designed to protect your valuable data and programs, as well as keep itself up-to-date and has the kind of built-in features that many vendors charge for additionally, or don't include at all.
Avast! Pro. v. 4.8.1287Professional Edition is a collection of high-end technologies that work in perfect synergy, having one common goal: to give you the top grade protection against computer viruses. It represents an ideal solution for any Windows-based workstation.
Avast! Pro. v. 4.8.1287 Professional Edition is a complete ICSA certified antivirus software for your company. It obtained VB100% awards in 2002/4 Virus Bulletin comparative reviews.
avast! scans for viruses, worms and Trojans: On Demand - with two User Interfaces, On Access, E-mail, during Boot Time, in File Explorer and Screen Saver. It maintains Virus Chest. Protects E-mail, HTTP, NNTP, ICQ, mIRC, Kazaa etc. True incremental updates based on iAVS technology updates twice a week virus definition file.
Avast Pro 2009 v.4.8.1287 ! Professional Supports the32 & 64-bit Windows Vista & XP platforms.
Features:
* Antivirus kernel
* Simple User Interface
* Enhanced User Interface
* Resident protection
* Script Blocker (Professional Edition only
* P2P and IM Shields
* Network Shield
* Web Shield
* Automatic updates
* PUSH updates
* Virus Chest
* System integration
* Command-line scanner
* Integrated Virus Cleaner
* Support for 64-bit Windows / Vista
* Internationalization
*** Antivirus Kernel
New version of avast! antivirus kernel features outstanding detection abilities, together with high performance. You can expect 100% detection of In-the-Wild viruses (the ones what are really spreading amongst people) and very good detection of Trojan horses, all that with only a minimum number of false alarms.
The kernel was certified by ICSA; it frequently takes part in the tests of Virus Bulletin magazine, often yielding the VB100 award.
*** Simple User Interface
Simple User Interface is used to start on-demand scanning, work with the results, change various options etc. Basic resident protection settings can be modified here. Simple User Interface is the main application of avast! 4 Home Edition. You can start additional avast! modules from here, such as the Virus Chest, Updater or Log Viewer.
*** Enhanced User Interface
Unlike the Simple User Interface, the scanning is performed by so called "tasks". First, you define a task, including various parameters - areas to scan, what to scan, how to scan, etc. Having the task, you can (possibly repeatedly) run it. Each task generates a list of results; you can work with them later.
*** Resident protection
Resident protection, i.e. the real-time protection of the computer, is one of the most important parts of an antivirus program today. avast! features a powerful resident module that is able to detect the virus before it has any chance to infect your computer.
E-mail protection consists of two independent modules; first, there is a generic scanner working on the SMTP/POP3/IMAP4 protocol level. It is capable of protecting any existing e-mail client that uses these protocols. Second, there is a special plug-in for MS Outlook only; it is completely transparent, requiring no special settings.
New feature of version 4 is heuristic analysis of e-mail scanners. It is extremely useful in protecting against new, unknown viruses and worms that are not possible to detect by the usual means. The heuristic module performs a thorough investigation of every e-mail message and watches for suspicious signs that might announce virus presence. When the number of those signs exceeds the user-defined level, the message is considered dangerous and the user is warned.
*** Script Blocker
The resident protection of the Professional Edition includes an additional module, not contained in the Home Edition - Script Blocker. This module watches all the scripts being executed in the operating system (so called WSH scripts - Windows Scripting Host). It also scans all the scripts run as a part of a web page within your web browser (Internet Explorer, Netscape Navigator and Mozilla).
*** Automatic updates
Automatic updates are another key point in virus protection. Both the virus database and the program itself can be updated automatically.
*** PUSH updates
A special feature of the Professional Edition are PUSH updates. It is a dramatic change in the philosophy of updates. Usually, every installed program checks every now and then whether a new version is available. PUSH updates, however, are initialized by our server; they result in your computer quickly responding and performing the necessary update. The system is based on the SMTP protocol, i.e. on usual e-mail messages. The updates itself are controlled by the avast! resident e-mail providers (MS Outlook and Internet Mail).
*** Virus Chest
The main properties of the Virus Chest are complete isolation from the rest of the operating system (no outside process, i.e. no virus either, may access the files inside) and the fact that the files inside the Chest may not be run (i.e. there is no danger in storing viruses there).
*** System integration
avast! antivirus features outstanding integration into your system. The scanning can be started directly from Windows Explorer, by clicking a folder or a file with your right mouse button and selecting the corresponding choice from the menu.
Another interesting feature is a special screen-saver that performs scanning for viruses during its run-time. avast! antivirus works together with your favorite screen-saver, so you don't have to change to anything you wouldn't like.
Another new option is the boot-time scan (Windows NT/2000/XP/.NET only). It is important in the case that a virus is suspected to be active on your computer. The boot-time scan is performed before the virus may get activated, so the virus cannot influence the scanning in any way.
*** Command-line scanner
Experienced users may like another Professional Edition feature - command-line scanner. The scanning can be controlled by many arguments and switches; to use as a pipe filter, a special STDIN/STDOUT mode is available.
The module is intended to be used in BATCH programs. Its output is the same as the output from the Enhanced User Interface tasks (including the report files).
Product Website:
http://www.avast.com/
OS: Windows XP, Vista

Download Link:
Comment me! Ill send you the link:
Posted on
by
j lo,
under
all-in-one,
antivirus,
security and protection,
software.
0
comments.
![]()
Protect yourself from the Conficker computer worm
The Conficker worm is a computer worm that can infect your computer and spread itself to other computers across a network automatically, without human interaction.
If you are an IT professional, please visit Conficker Worm: Help Protect Windows from Conficker.
Am I at risk of having the Conficker worm?
Most antivirus software could detect and block the Conficker worm, so if you have updated antivirus software on your computer, you are at a much lower risk of being infected by the Conficker worm.
If you or your network administrator have not installed the latest security updates from Microsoft and your antivirus provider, and if you have file-sharing turned on, the Conficker worm could allow remote code execution. Remote code execution allows an attacker to take control of your computer and use it for malicious purposes.
What does the Conficker worm do?
To date, security researchers have discovered two variants of the worm in the wild.
| • | Win32/Conficker.A was reported to Microsoft on November 21, 2008. |
| • | Win32/Conficker.B was reported to Microsoft on December 29, 2008. |
| • | Win32/Conficker.C was reported to Microsoft on February 20, 2009. |
| • | Win32/Conficker.D was reported to Microsoft on March 4, 2009. |
Win32/Conficker.B might spread through file sharing and via removable drives, such as USB drives (also known as thumb drives). The worm adds a file to the removable drive so that when the drive is used, the AutoPlay dialog will show one additional option.
The Conficker worm can also disable important services on your computer.
In the screenshot of the Autoplay dialog box below, the option Open folder to view files — Publisher not specified was added by the worm. The highlighted option — Open folder to view files — using Windows Explorer is the option that Windows provides and the option you should use.
If you select the first option, the worm executes and can begin to spread itself to other computers.

The option Open folder to view files — Publisher not specified was added by the worm.
How does the Conficker worm work?
Here’s an illustration of how the Conficker worm works.

How do I remove the Conficker worm?
If your computer is infected with the Conficker worm, you may be unable to download certain security products, such as the Microsoft Malicious Software Removal Tool or accessing certain Web sites, such as Microsoft Update. If you can't access those tools, try using the Windows Live OneCare Safety Scanner.Where can I find more technical information about the Conficker worm and how can I stay up to date on the Conficker worm?
| • | For additional information, see Centralized Information About the Conficker Worm. |
| • | For more technical information about the Conficker worm, see the Microsoft Malware Protection Center Virus Encyclopedia |
| • | Bookmark the Microsoft Malware Protection Center portal and the Microsoft Malware Protection Center blog for updated information. |
| • | For symptoms and detailed information about how to remove the Conficker worm, see Help and Support: Virus alert about the Conficker Worm. |
| • | To continue to get updated information on security, sign up for the Microsoft Security for Home Computer Users newsletter. |
For more information, see How to prevent computer worms and How to remove computer worms.
source: http://www.microsoft.com/protect/computer/viruses/worms/conficker.mspx
Posted on
Wednesday, April 01, 2009
by
j lo,
under
general info.,
knowledge database,
microsoft,
tutorials,
windows.
0
comments.
![]()
Rowse polled both his ProBlogger audience (which is presumably comprised mainly of bloggers) and his Twitip audience (which is made up of Twitterers). As expected, the Twitip crowd favored Twitter followers slightly more, but there was still a very clear majority wanting more blog readers. Rowse provides the following graphs:
There are certainly arguments for the value of both categories, and Rowse covers them pretty well here. There are some pretty obvious ones for blogs:
There are obvious benefits to having Twitter followers too though, particularly for marketers.
Of course people who both blog and tweet know they don't have to choose between one medium or the other. They compliment each other, and ideally can work to each other's benefits. Twitter can gain you more blog readers, and a blog can gain you more Twitter followers.It's all in the execution. Write good content that Twitterers want to link to. This has plenty of potential for getting you more readers. Include chiclets on your posts, making it easy to share your content (this shouldn't be limited to Twitter). Include a prominent link for people to follow you on Twitter (a Twitter logo here will help draw attention).
Link to good content from others when you Tweet. If people like what you're pointing them to, you'll likely gain more followers. Who would've guessed it all comes back to content? You could also mention your blog casually from time to time. This may increase awareness of it. Just because someone follows you on Twitter, does not mean they know about your blog. That said, you probably don't want to ram it down their throats either.
So, blogging Twitter users, would you rather have more blog readers or Twitter followers? Tell us.
source: http://www.webpronews.com